Internet Misuse in the Workplace
Tuesday, May 31, 2016
Please see www.keeganskeate.com for my most recent work.
Tuesday, April 9, 2013
Time Wasting and Productivity Cont.
With technology today, opportunities and unfavorable circumstances are created especially in a place of business. Technology has improve communication networks, attracting human capital, enhanced efficiency, and etc. On the other hand, technology can cause communication breakdowns, increase the input level of stress, distractions, and so on and so forth.
Looking at the unenthusiastic side of technology, the questions becomes "Exactly how much time productive time is wasted at work?" According to recent article 2013 Wasting Time at Work Survey, written by Aaron Gouveia, their survey respondents said:
0-30 Minutes 34%
30-60 Minutes 24%
Several Hours a Day 11%
1-2 Times a Week. 21%
Claimed to Never 10%
"When we last did this survey in 2012, 64% of our survey respondents said they waste time at work on a daily basis. This year that number is on the rise as 69% of the people surveyed in 2013 said they waste time at work every single day. (Aaron Gouveia). This results clearly presents as technology advances so does resisting weakness.
Even if companies/organizations are to block personal websites on their work computers, employees still have their smart phones enabling the use of mobile applications at the touch of their finger tips. But why are employees are wasting so much valuable time on non-related work matters. Lets look at Dan Malachowsi top five time wasting excuses:
Don't have enough work to do 33.2%
Underpaid for amount of work 23.4%
Co-workers distract me 14.7%
Not enough after-work time 12.0%
Other 16.7%
Throughout my research there were many and more excuses that were used but I decided to use Malachowsi due to simplistic reasoning and what I would I personally choose as an excuse.
Looking at the unenthusiastic side of technology, the questions becomes "Exactly how much time productive time is wasted at work?" According to recent article 2013 Wasting Time at Work Survey, written by Aaron Gouveia, their survey respondents said:
0-30 Minutes 34%
30-60 Minutes 24%
Several Hours a Day 11%
1-2 Times a Week. 21%
Claimed to Never 10%
"When we last did this survey in 2012, 64% of our survey respondents said they waste time at work on a daily basis. This year that number is on the rise as 69% of the people surveyed in 2013 said they waste time at work every single day. (Aaron Gouveia). This results clearly presents as technology advances so does resisting weakness.
Even if companies/organizations are to block personal websites on their work computers, employees still have their smart phones enabling the use of mobile applications at the touch of their finger tips. But why are employees are wasting so much valuable time on non-related work matters. Lets look at Dan Malachowsi top five time wasting excuses:
Don't have enough work to do 33.2%
Underpaid for amount of work 23.4%
Co-workers distract me 14.7%
Not enough after-work time 12.0%
Other 16.7%
Throughout my research there were many and more excuses that were used but I decided to use Malachowsi due to simplistic reasoning and what I would I personally choose as an excuse.
http://www.salary.com/2013%2Dwasting%2Dtime%2Dat%2Dwork%2Dsurvey/slide/2/
http://www.davidsonstaffing.com/articles/salary/wasted-time/
http://www.davidsonstaffing.com/articles/salary/wasted-time/
Mobile Devices Internet Misuse
The image of workplace Internet misuse is often the one of
an employee in an office environment using a desktop computer to access the Internet
for matters not related to work. The truth is that mobile Internet devices,
such as smart phones and tables, give employees the chance to misuse the
Internet off company property. The most common example of how an employee
mobile internet misuse can affect a company both legally and financially is the
case of a employee using a company provided mobile phone to access the internet
while driving a company vehicle. Common sense tells us that we should not use
mobile phones to access the Internet or send text messages while driving, but
we know that it occurs quite regularly. Employee caused accidents usually
affect companies legally and financially regardless of whether the accidents
occur on company property or off company property.
(http://www.thehindu.com/multimedia/dynamic/00873/TH25_THERN_MOBILE_873679f.jpg)
According to the government site Distracted.gov the three
primary laws in North Carolina regarding mobile phone usage are: “Ban on all
cell phone use (handheld and hands-free) for bus drivers (Primary law), Ban on
all cell phone use (handheld and hands-free) for novice drivers (Primary law),
and Ban on texting for all drivers (Primary law)”
(http://smallbusiness.chron.com/DM-Resize/photos.demandstudios.com/getty/article/151/184/87785452.jpg?w=600&h=600&keep_ratio=1)
Mobile Internet devices increase the likelihood of employees
releasing confidential company and customer information often unintentionally.
Mobile phones allow employees to post different types of media online in just a
few seconds. An unauthorized workplace picture, tweet, Facebook post, YouTube
video, or other release of company information through a social media website
could cause extreme damage to a company both legally and financially depending
on the industry and the type of information released.
Websites of interest
Sunday, April 7, 2013
Cyber Crime: Phishing Attacks
Many unknowing employees are exposing confidential information on company computers, simply by using personal email. The danger is from phishing attacks; fraudulent emails with intent to extract financial data. They lure recipients in with false claims and official-looking emails. With just a click, malware is uploaded and cyberheist has begun. Customer data, credit card, bank account, and Social Security numbers can all be obtained. This can be a serious threat. Certain industries make prime targets and are more at risk than others. You'll be surprised to find out who is vulnerable to phishing attacks.
In a recent research study, by KnowBe4, several thousand companies were targeted to see if they were safe from cyber criminals. Small, fast-growing businesses from the Inc. 5000 list were chosen, and publicly available information was gathered. Domain names and email addresses, easily accessed over the Internet, were obtained and some 28,000+ emails were sent. Each email was a simulated phishing attack that did not have a malicious payload. The results were shocking, within a couple hours half of all the emails had been opened. Of the emails opened, employees from about 500 companies clicked the phishing attack link, exposing private company information. Before the study's IP address was shut down, they had been able to gather data for about 21 hours. This can have serious consequences. It is estimated that small-businesses lose more than $40 million a year to cyber crime. A growing problem, cyber criminals target smaller businesses and banks in particular due to low investment in IT. The industries found most susceptible to attack were; travel, education, finance, government services, and in fact IT services.
It is scary to think that so many businesses are at risk, yet employees are unaware. The CEO of KnowBe4, Stu Sjouwerman, said, "Most people assume that antivirus software and an in-house IT team provide sufficient data security, but considering that IT is among the most phish-prone industries, it's clear that's a very dangerous assumption to make." Most people at work do not consider the risks they may be exposing the company to while being on the Internet. Simply opening strange emails can have severe repercussions. Cyber crime is a very profitable growing industry, and should be a major concern for small businesses. Proper training, education, and prevention is crucial for combating cybercriminals.
Articles of Interest and Sources
http://jobs.aol.com/articles/2011/05/24/you-could-be-inviting-scammers-into-your-workplace/ (news article)
http://www.knowbe4.com/fail500/ (research study)
http://dictionary.reference.com/browse/phishing
In a recent research study, by KnowBe4, several thousand companies were targeted to see if they were safe from cyber criminals. Small, fast-growing businesses from the Inc. 5000 list were chosen, and publicly available information was gathered. Domain names and email addresses, easily accessed over the Internet, were obtained and some 28,000+ emails were sent. Each email was a simulated phishing attack that did not have a malicious payload. The results were shocking, within a couple hours half of all the emails had been opened. Of the emails opened, employees from about 500 companies clicked the phishing attack link, exposing private company information. Before the study's IP address was shut down, they had been able to gather data for about 21 hours. This can have serious consequences. It is estimated that small-businesses lose more than $40 million a year to cyber crime. A growing problem, cyber criminals target smaller businesses and banks in particular due to low investment in IT. The industries found most susceptible to attack were; travel, education, finance, government services, and in fact IT services.
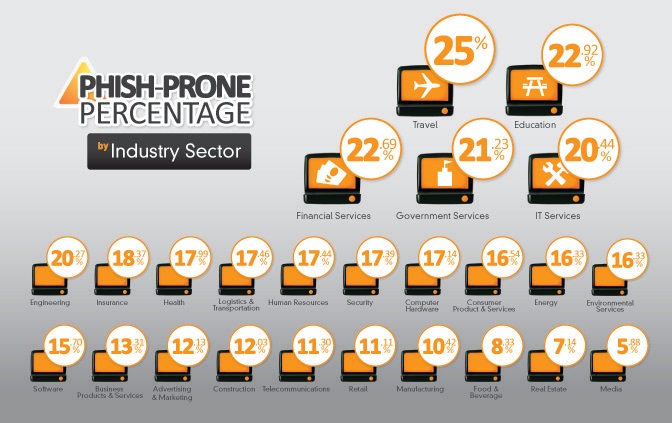 |
| (https://s3.amazonaws.com/knowbe4-images/KnowBe4+WP+Images/Fail500IndustryGraph.jpg) |
Articles of Interest and Sources
http://jobs.aol.com/articles/2011/05/24/you-could-be-inviting-scammers-into-your-workplace/ (news article)
http://www.knowbe4.com/fail500/ (research study)
http://dictionary.reference.com/browse/phishing
Saturday, March 30, 2013
Internet Misuse in the Workplace: Internet Usage Monitoring
Another prevention method for employers is implementing software that monitors employees’ internet searching. This will allow managers to monitor the employees and when a manager finds the employee is not doing what they are supposed to be doing, they can hold that employee accountable for their actions. The consequence could be coaching them, providing disciplinary action, or terminating them depending on the internet usage policy of the company. When coaching an employee the company representative needs to ensure that they don’t threaten actions they are unwilling to follow through with or are not in line with company policy.
The website below lists the Top Ten Employee Monitoring Software Programs you can purchase, which highlights these top three monitoring softwares:
1) SONAR
2) Spector CNE Investigator
3) Spytech NetVizor
http://employee-monitoring-software-review.toptenreviews.com/
There are some downsides to internet usage monitoring. For instance, companies will have to pay another employee to monitor employees’ actions, so the company will either end up losing money to ensure its employees stay productive or losing money through the loss of productivity of its employees while they surf the internet. In the latter instance, employers always have the option to performance manage their employees if they are not finishing their work timely.
In conclusion, you need to identify the problem and take the appropriate actions, whether that is educating your employees or implementing monitoring software to monitor the employees’ actions.
Cited
http://www.techsupportalert.com/pdf/m1847.pdf
Internet Misuse in the Workplace: Prevention
In this portion of the blog I will discuss how to deal with internet abusers and what you can do to prevent people from abusing the internet at the workplace.
First, if you are in a leadership role, working for a company that does not allow internet misusage at the workplace, you need to make sure that you inform your employees of the internet usage policies when they are first hired. The best time for this would be during new employee training before the employee even starts with the company. Set the expectation up front. Most jobs now require a computer and access to the internet, so if you want your employees to concentrate on work, you need to put this in the internet usage policy and make sure they sign the policy saying they read the terms and conditions. If you don’t proactively inform your employees of your policies, it is much more likely that you will see misusage on a daily basis. Look at the numbers from an earlier post.
In my opinion, you need to stop misuse from happening the first time you see it. If you don’t address it immediately when you initially identify the issue, employees will continue abusing the policy throughout their employment because they think they can get away with it. Consistent enforcement of the policy is also important to ensure that people understand the consequences of inappropriate internet usage and see that the company does take the internet abuse policy seriously for all employees in all cases.
Cited
Saturday, March 23, 2013
Solutions to Social Media Misuse in the Workplace:
Now that we have talked about Social media misuse in the workplace, we are now going to focus on some different solutions to it.
A lot of employers find themselves asking questions such as:
What can you do as an employer to prevent social media misuse in the workplace?
One way to stop social media misuse and posting of confidential information would be to implement Social Media Policies. These policies should be read and agreed upon before the potential employee or current employee can continue to work. The policies should clearly state the rules and regulations to what is appropriate to do while working for the company.
Employers should also be sure to inform their employees on the difference between speaking on the behalf of their company's and what is speaking about the company.
Also, I feel that employers should have monitors on all employees allowing them to access social media sites only on their personal computers and smart phones. This would help with employees staying focused while they are at work.
I think that if these policies are set in place employers can minimize the misuse of social media in the workplace and they will find that all employees will be more effective and efficient.
I found this picture of how to train your employees when using social media very helpful.
Check it out and tell me what you think!
Now that we have talked about Social media misuse in the workplace, we are now going to focus on some different solutions to it.
A lot of employers find themselves asking questions such as:
What can you do as an employer to prevent social media misuse in the workplace?
One way to stop social media misuse and posting of confidential information would be to implement Social Media Policies. These policies should be read and agreed upon before the potential employee or current employee can continue to work. The policies should clearly state the rules and regulations to what is appropriate to do while working for the company.
Employers should also be sure to inform their employees on the difference between speaking on the behalf of their company's and what is speaking about the company.
Also, I feel that employers should have monitors on all employees allowing them to access social media sites only on their personal computers and smart phones. This would help with employees staying focused while they are at work.
I think that if these policies are set in place employers can minimize the misuse of social media in the workplace and they will find that all employees will be more effective and efficient.
I found this picture of how to train your employees when using social media very helpful.
Check it out and tell me what you think!
Tuesday, March 19, 2013
Social Media Misuse in the Workplace:
Social Media has surrounded and shaped our way of doing anything these days. Many people feel that without it they are hopeless. They have turned social media into a daily routine and now they are taking it into their workplace.
But there are not only risk of wasting time on social media in the workplace, there are also various cases of employees terminated for posting rude and inappropriate posts to their Facebook's and Twitter's about their employers.
On the other hand there are positive outcomes to having Social Media in the workplace because your employees are making and maintaing connections with people all around the world which could be good for networking strategies.
According to the Conference Agenda, as social networking takes over every employer and business owner is going to have to find a way to control data and social media by showing in this session:
Here is a video to show how social networking dangers in the workplace:
Cited:
Social Media has surrounded and shaped our way of doing anything these days. Many people feel that without it they are hopeless. They have turned social media into a daily routine and now they are taking it into their workplace.
But there are not only risk of wasting time on social media in the workplace, there are also various cases of employees terminated for posting rude and inappropriate posts to their Facebook's and Twitter's about their employers.
On the other hand there are positive outcomes to having Social Media in the workplace because your employees are making and maintaing connections with people all around the world which could be good for networking strategies.
According to the Conference Agenda, as social networking takes over every employer and business owner is going to have to find a way to control data and social media by showing in this session:
- how to develop and implement internet and social media policies
- strategies and punishments for time theft, during or after work hours
- lesson on how to terminate and when to evaluate performance
Here is a video to show how social networking dangers in the workplace:
Cited:
- http://www.staffmonitoring.com/P32/abuse.htm
Monday, March 18, 2013
Cyber Crime: ICE Scam Alert
All Internet users have experienced a bombardment of advertisements at some point while surfing the web. Pop-up advertisements can be annoying, harassing, and sometimes even dangerous. It is often difficult to tell the legitimacy of these advertisements, and many boast false claims. There is a new breed of fraudulent Internet advertisements, e-scams. They are used to take advantage of Internet users by conducting sham transactions, stealing personal information, and extorting money. Found on websites, ads, emails, and downloaded malware, they come in many forms. E-scams are deceptive, harmful, and illegal. Internet fraud has become a serious problem that the government is addressing.
The U.S. Immigration and Customs Enforcement, or ICE, is the main government department responsible for controlling Internet crime. They deal with such issues as online child abuse, money laundering, arms and drugs trafficking, intellectual property rights, and identity theft. Cyber Crime is a wide-scope issue, and Internet scams are a major part. The latest is e-scam is a drive-by downloaded malware that installs itself onto the users computer. The malware then freezes the computer, claiming the user committed federal crimes, and demands the user must pay the ICE $400 within 48 hours. It is completely fictitious, a hoax, and is considered ransomware. Once downloaded, it requires a computer expert to remove. The ICE has released a warning against this scam and others like it. They let you know how to identify current e-scams, protect yourself, as well as give suggestions for victims. To check out the latest dangerous e-scams, you can go to the FBI's E-scams and warnings page.
In today's online world, it is important that users educated themselves against Internet fraud. From being able to identify a fictitious advertisement, to being able to deal with threats from malware. E-scams are real, and can be very harmful. They are a serious problem that all users need to be aware of.
Articles of Interest
Friday, March 15, 2013
Legal and Financial Impact
We often associate the unauthorized release of confidential company information with actions from hackers and undercover agents from competitors, but the truth is that a large percentage of the unauthorized release of information is related to Internet misuse in the workplace. Even though most companies have strict Internet usage policies their employees frequently disregard these policies. According to a study from Websense Inc. “employees are using the Web more and more for personal reasons and that is setting U.S. companies back $178 billion annually, a cost of $5,000 per employee.”
| (http://www.brcontrol.com.br/ENG/images/browser-logo-major.jpg) |
An example of how Internet misuse in the workplace has the
ability to affect a company both legally and financially is the case of an
employee from a medical facility using the Internet to post a comment on a
social media website regarding a patient. Even if the employee and the patient
are related and the employee did not have any negative intentions the
unauthorized release of medical information represents a Health Insurance Portability and
Accountability Act (HIPAA) violation. HIPAA violations represent high financial
and legal costs to the health industry.
HIPPA compliance program advertisement
| (http://abouthipaa.com/wp-content/uploads/dothemath-bootcamp.jpeg) |
Even though some companies cannot restrict their employees’
access to the Internet because of the nature of their business, the companies
have the chance to establish solid ethics and compliance policies and training.
Effective ethics and compliance programs lower the legal and financial impact
of a data breach on a company because the companies that use them the have the
ability to prove that they took reasonable measures to prevent the data
breaches.
Websites of interest
Subscribe to:
Comments (Atom)


